Data Protection
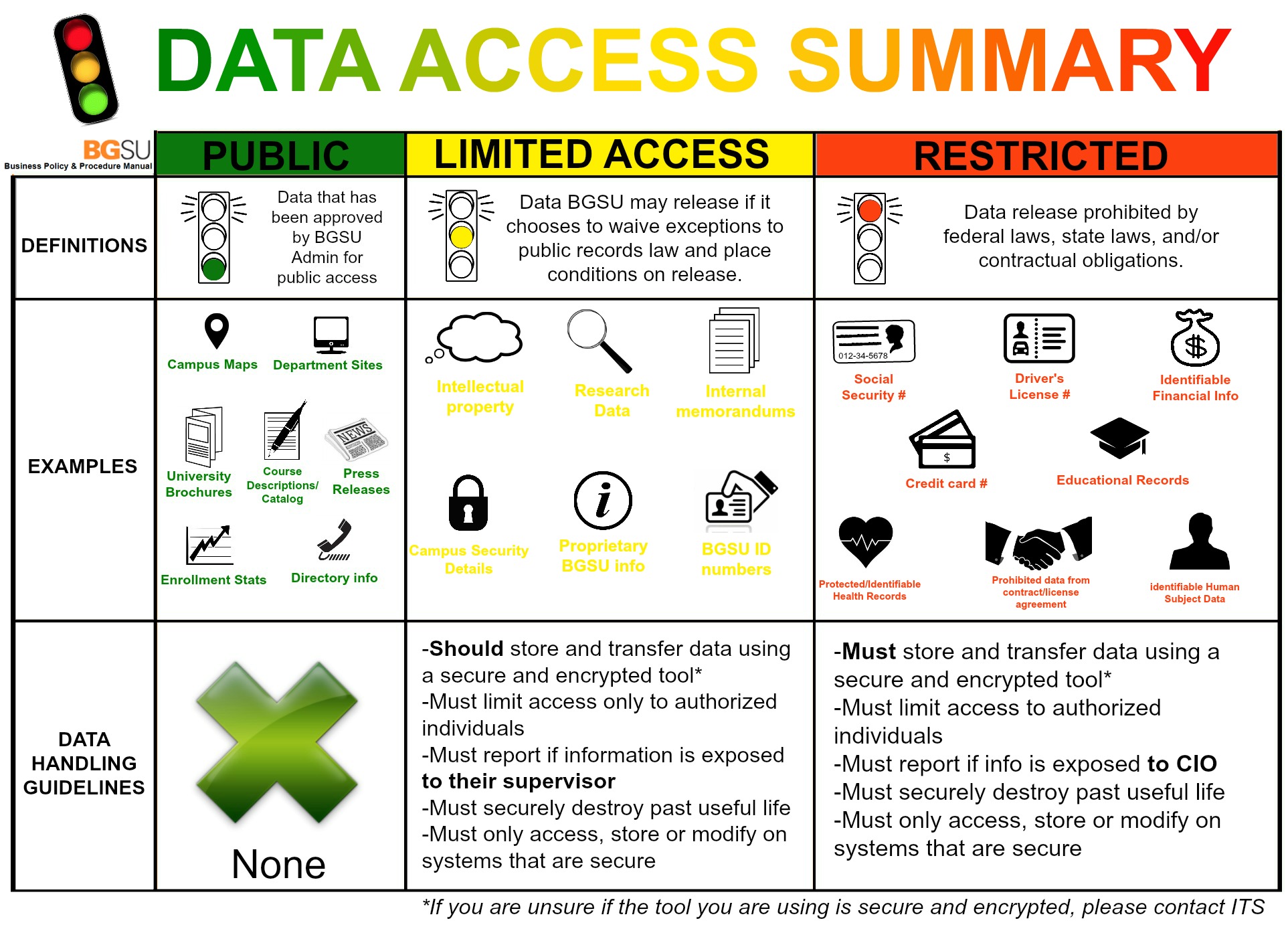
In the course of doing business, University employees may need to collect, store, process and transmit data that REQUIRES protection from unauthorized exposure. The graphic below will help you to determine how best to handle the storing and sending of specific data types.
For a comprehensive summary of various types of data and BGSU recommended methods for protecting this data, please review our Data Resource Summary.
Data Resource Summary: Appendix A
| PUBLIC | LIMITED ACCESS | RESTRICTED | |
| DEFINITIONS | Data that has been approved by BGSU Administration for public access. | Data BGSU may release if it chooses to waive exceptions to the public records law and place conditions or limitations on such release. Notification of unauthorized access is not required to the victims or other outside entities. | Data release prohibited by federal laws, state laws, and/or contractual obligations. For data to be defined as restricted, notification of unauthorized access is required to the victims or other outside entities. |
EXAMPLES (This list has been created to provide examples and should not be considered as complete. It is the responsibility of each data owner to determine the classification.) |
|
|
|
DATA HANDLING GUIDELINES |
|
|
|
*This chart is a summary of data classification and handling of data at BGSU. For more details on data classification and information on the appropriate data handling, please visit the Data Use & Protection policy and Sensitive Data Privacy policy.
Sensitive Data Storage References
Fore best practices and policies relating to storing sensitive information at BGSU, please review the links below.
Updated: 05/16/2023 04:29PM